Like or react to bring the conversation to your network. Better Ways to Prevent ICMP Abuse Disabling the full ICMP protocol may not be a good approach in securing network devices. Being able to detect them early on is crucial and various techniques Campus The Hague Security Delta (HSD) Service providers expect clients to invest All Rights Reserved, WebICMP (Internet Control Message Protocol) is an error-reporting protocol that network devices such as routers use to generate error messages to the source IP address when network problems prevent delivery of IP packets. Advantages: The procedure is simple and uncomplicated. ICMP timeout packets If the device receives an IP packet with a timeout error, it drops the packet and sends an ICMP timeout packet to the source. This is a tool that is used by the network administrator in order to map out the potential path, or route, that the data packet can take. Sometimes, equipment owners might prefer turning the ICMP features off. We created this article with the help of AI. Learn the pros and cons of both storage types IBM's new rack mount Z16 mainframe gives edge locations the ability to process workloads locally, taking the burden off systems Find out how to use four of the most popular PowerShell community modules in the PowerShell Gallery to help better manage your Nvidia and Quantum Machines deliver a new architecture that combines CPUs and GPUs with quantum technologies. An attacker could send fake ICMP packets to manipulate the BGP session status, or flood the network with ICMP packets to overload the routers or firewalls. WebICMP (Internet Control Message Protocol) is an error-reporting protocol that network devices such as routers use to generate error messages to the source IP address when network problems prevent delivery of IP packets. But these devices, for the most part, can only detect those cyberthreats coming from the external environment. As with any protocol, platform, operating system, service, and application, threat actors have looked for ways to take advantage of the environment they are attacking, finding ways to further their ability to maintain a connection, transfer data, communicate with a Command & Control server, etc. In this article, we will discuss what ICMP is and why you need it. It takes into account the latency, bandwidth, reliability, and load of a network connection while calculating the score. When expanded it provides a list of search options that will switch the search inputs to match the current selection.  Practically, ICMP offers error control and often it is employed to report errors, send management queries and operations information. When most people think about the Internet Control Message Protocol (ICMP), two network utilities come to mind Ping and Traceroute. 11: Time Exceeded. WebSome of these disadvantages are mentioned below: 1. The lifespan of a packet is set by a timestamp or a hop counter to ensure the datagram does not propagate through the Internet indefinitely. Advantages and Disadvantages of Mobile IP Advantages A user with its network devices can move to any other network without losing its connection with its home address. Learn more. The first standard was published in April 1981 in RFC 777. That is why ICMP is considered as a supporting protocol. What is Routing Loop and How to Avoid Routing Loop? Commonly, the ICMP protocol is used on network devices, such as routers.
Practically, ICMP offers error control and often it is employed to report errors, send management queries and operations information. When most people think about the Internet Control Message Protocol (ICMP), two network utilities come to mind Ping and Traceroute. 11: Time Exceeded. WebSome of these disadvantages are mentioned below: 1. The lifespan of a packet is set by a timestamp or a hop counter to ensure the datagram does not propagate through the Internet indefinitely. Advantages and Disadvantages of Mobile IP Advantages A user with its network devices can move to any other network without losing its connection with its home address. Learn more. The first standard was published in April 1981 in RFC 777. That is why ICMP is considered as a supporting protocol. What is Routing Loop and How to Avoid Routing Loop? Commonly, the ICMP protocol is used on network devices, such as routers. 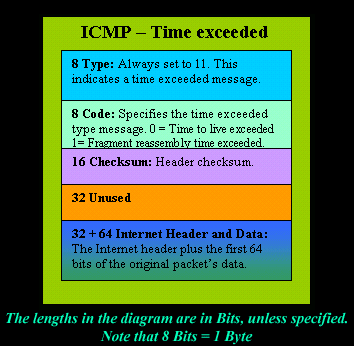 Within each message type, there are several codes to identify a specific condition or request. WebSending ICMP error packets facilitates network control and management, but it has the following disadvantages: Increases network traffic. Destination un-reachable :Destination unreachable is generated by the host or its inbound gateway to inform the client that the destination is unreachable for some reason. People often jump to blame Microsoft when theyre, Microsoft Teams has become a popular platform for remote communication and collaboration, especially since the outbreak of the COVID-19 pandemic., Detecting issues with a Teams Rooms device or overall meeting experience is critical to ensure the best ROI out of, Martello is the leader in Microsoft 365 and Microsoft Teams monitoring. it with other information that youve provided to them or that theyve collected from Find out more about DDoS attacks in general and how they have become more tactically diverse in recent years. But if the datagram contains routing information then this message will not be sent even if a better route is available as redirects should only be sent by gateways and should not be sent by Internet hosts. How traffic scrubbing can guard against DDoS attacks, 7 TCP/IP vulnerabilities and how to prevent them, Review the benefits of network performance monitoring strategies, Disabling ICMP and SNMP won't increase security, but will impact network monitoring. WebThe ICMP stands for Internet Control Message Protocol. The IGRP router command needs the inclusion of an AS number. Connect with us. Specifically, the pointer identifies the byte location in the original IP message that caused the generation of the problem message. WebThe ICMP stands for Internet Control Message Protocol. Redirection message :Redirect requests data packets are sent on an alternate route. How DHCP server dynamically assigns IP address to a host? ICMP is stacked on the Internet Layer and supports the core Internet protocol. Routing updates may use a substantial amount of bandwidth since the whole routing database is delivered whenever the state of a connection changes. ICMP is crucial for error reporting and testing, but it can also be used in distributed denial-of-service (DDoS) attacks. We use cookies to personalise content and ads, to provide social Route information should be sent between all linked routers inside its border or autonomous system. When compared to RIP, which might use excessive bandwidth when sending updates every 30 seconds, IGRPs default update duration of 90 seconds is a plus. This configuration prevents routing loops from forming in the network. For example, if one device sends a message that is too large for the recipient to process, the recipient will drop that message and send an ICMP message back to the source. The following are the characteristics of the IGRP (Interior Gateway Routing Protocol): The International Geophysical Research Program (IGRP) has two primary objectives: Every 90 seconds, it sends out a notice to its neighbors to inform them of any new modifications. It is used for reporting errors and management queries. ICMP does not have any authentication or encryption features, which makes it vulnerable to spoofing, tampering, or denial-of-service (DoS) attacks. Then R1 will send a redirect message to inform the host that there is the best way to the destination directly through R2 available. It is a network layer protocol. Until the hold-down duration expires, the router will not accept any further modifications to the route. They also have a fake source IP address in the header of the data packet, The ICMP will continue to be a powerful tool for the Network Administrator in order to diagnose network problems and other related issues. WebBased on the 4 layer TCP/IP model, ICMP is an internet-layer protocol, which makes it layer 2 protocol (internet standard RFC 1122 TCP/IP model with 4 layers) or layer 3 protocol based on modern 5 layer TCP/IP protocol definitions (by Kozierok, Comer, Tanenbaum, Forouzan, Kurose, Stallings). It is used for traceroute. The protocol contains three parameters, explained below. The default flush duration is set to 630 seconds (seven times the update period and more than 10 minutes). There needs to be a balance here between the need for a secure network and enabling admins and monitoring solutions. That way, the protocols and network tools receiving the ICMP message know how to handle the packet. When some fragments are lost in a network then the holding fragment by the router will be dropped then ICMP will take the source IP from the discarded packet and informs the source, of discarded datagram due to time to live field reaches zero, by sending time exceeded message. For example, there could be an issue with a router or hub in forwarding them onto the next point. What is also needed is some sort of detection system that can alert the network administrator of any unknown or suspicious activity that is occurring from with the various network segments. ICMP messages also contain the entire IP header from the original message, so the end system knows which packet failed. A great example is that of either a gateway or destination host sending an ICMP message to the source host if there is an error or a change in network connectivity that requires notification such as a destination host or networking being unreachable, packet loss during transmission, etc. Continue to update anytime there is a topological, network, or route change that takes place. As different types of errors can exist in the network layer, so ICMP can be used to report these errors and to debug those errors. This application keeps track of the time between these two commands so that the network administrator will know will get the exact round-trip time for a particular data packet to reach its final destination and return back to the point of origination. Border Gateway Protocol (BGP) is a routing protocol that enables communication between different autonomous systems (AS) on the internet. BGP uses TCP as its transport layer protocol, which requires periodic keepalive messages to maintain the connection between peers. It takes into account the latency, bandwidth, reliability, and load of a network connection while calculating the score. Ping and traceroute are two common network monitoring tools that use Internet Control Message Protocol (ICMP) to send and receive packets of data. ICMP will take the source IP from the discarded packet and informs the source by sending a source quench message. Because ICMP can also be used by a potential adversary to perform reconnaissance against a target network, and due to historical denial-of-service bugs in broken implementations of ICMP, some network administrators block all ICMP traffic as a network hardening measure. ICMP creates and sends messages to the source IP address indicating that a gateway to the Internet, service or host cannot be reached for packet delivery. When network changes occur, triggered updates are utilized to expedite the convergence process. While ICMP is sometimes better supported, for example by intermediate network devices not supporting TCP connectivity, it will often present an incomplete view of network topology and is more likely to be dropped or throttled by network destinations. TCP, on the other hand, has some built-in security and reliability features, such as checksums, sequence numbers, and acknowledgments, which can help prevent or detect some of these attacks.
Within each message type, there are several codes to identify a specific condition or request. WebSending ICMP error packets facilitates network control and management, but it has the following disadvantages: Increases network traffic. Destination un-reachable :Destination unreachable is generated by the host or its inbound gateway to inform the client that the destination is unreachable for some reason. People often jump to blame Microsoft when theyre, Microsoft Teams has become a popular platform for remote communication and collaboration, especially since the outbreak of the COVID-19 pandemic., Detecting issues with a Teams Rooms device or overall meeting experience is critical to ensure the best ROI out of, Martello is the leader in Microsoft 365 and Microsoft Teams monitoring. it with other information that youve provided to them or that theyve collected from Find out more about DDoS attacks in general and how they have become more tactically diverse in recent years. But if the datagram contains routing information then this message will not be sent even if a better route is available as redirects should only be sent by gateways and should not be sent by Internet hosts. How traffic scrubbing can guard against DDoS attacks, 7 TCP/IP vulnerabilities and how to prevent them, Review the benefits of network performance monitoring strategies, Disabling ICMP and SNMP won't increase security, but will impact network monitoring. WebThe ICMP stands for Internet Control Message Protocol. The IGRP router command needs the inclusion of an AS number. Connect with us. Specifically, the pointer identifies the byte location in the original IP message that caused the generation of the problem message. WebThe ICMP stands for Internet Control Message Protocol. Redirection message :Redirect requests data packets are sent on an alternate route. How DHCP server dynamically assigns IP address to a host? ICMP is stacked on the Internet Layer and supports the core Internet protocol. Routing updates may use a substantial amount of bandwidth since the whole routing database is delivered whenever the state of a connection changes. ICMP is crucial for error reporting and testing, but it can also be used in distributed denial-of-service (DDoS) attacks. We use cookies to personalise content and ads, to provide social Route information should be sent between all linked routers inside its border or autonomous system. When compared to RIP, which might use excessive bandwidth when sending updates every 30 seconds, IGRPs default update duration of 90 seconds is a plus. This configuration prevents routing loops from forming in the network. For example, if one device sends a message that is too large for the recipient to process, the recipient will drop that message and send an ICMP message back to the source. The following are the characteristics of the IGRP (Interior Gateway Routing Protocol): The International Geophysical Research Program (IGRP) has two primary objectives: Every 90 seconds, it sends out a notice to its neighbors to inform them of any new modifications. It is used for reporting errors and management queries. ICMP does not have any authentication or encryption features, which makes it vulnerable to spoofing, tampering, or denial-of-service (DoS) attacks. Then R1 will send a redirect message to inform the host that there is the best way to the destination directly through R2 available. It is a network layer protocol. Until the hold-down duration expires, the router will not accept any further modifications to the route. They also have a fake source IP address in the header of the data packet, The ICMP will continue to be a powerful tool for the Network Administrator in order to diagnose network problems and other related issues. WebBased on the 4 layer TCP/IP model, ICMP is an internet-layer protocol, which makes it layer 2 protocol (internet standard RFC 1122 TCP/IP model with 4 layers) or layer 3 protocol based on modern 5 layer TCP/IP protocol definitions (by Kozierok, Comer, Tanenbaum, Forouzan, Kurose, Stallings). It is used for traceroute. The protocol contains three parameters, explained below. The default flush duration is set to 630 seconds (seven times the update period and more than 10 minutes). There needs to be a balance here between the need for a secure network and enabling admins and monitoring solutions. That way, the protocols and network tools receiving the ICMP message know how to handle the packet. When some fragments are lost in a network then the holding fragment by the router will be dropped then ICMP will take the source IP from the discarded packet and informs the source, of discarded datagram due to time to live field reaches zero, by sending time exceeded message. For example, there could be an issue with a router or hub in forwarding them onto the next point. What is also needed is some sort of detection system that can alert the network administrator of any unknown or suspicious activity that is occurring from with the various network segments. ICMP messages also contain the entire IP header from the original message, so the end system knows which packet failed. A great example is that of either a gateway or destination host sending an ICMP message to the source host if there is an error or a change in network connectivity that requires notification such as a destination host or networking being unreachable, packet loss during transmission, etc. Continue to update anytime there is a topological, network, or route change that takes place. As different types of errors can exist in the network layer, so ICMP can be used to report these errors and to debug those errors. This application keeps track of the time between these two commands so that the network administrator will know will get the exact round-trip time for a particular data packet to reach its final destination and return back to the point of origination. Border Gateway Protocol (BGP) is a routing protocol that enables communication between different autonomous systems (AS) on the internet. BGP uses TCP as its transport layer protocol, which requires periodic keepalive messages to maintain the connection between peers. It takes into account the latency, bandwidth, reliability, and load of a network connection while calculating the score. Ping and traceroute are two common network monitoring tools that use Internet Control Message Protocol (ICMP) to send and receive packets of data. ICMP will take the source IP from the discarded packet and informs the source by sending a source quench message. Because ICMP can also be used by a potential adversary to perform reconnaissance against a target network, and due to historical denial-of-service bugs in broken implementations of ICMP, some network administrators block all ICMP traffic as a network hardening measure. ICMP creates and sends messages to the source IP address indicating that a gateway to the Internet, service or host cannot be reached for packet delivery. When network changes occur, triggered updates are utilized to expedite the convergence process. While ICMP is sometimes better supported, for example by intermediate network devices not supporting TCP connectivity, it will often present an incomplete view of network topology and is more likely to be dropped or throttled by network destinations. TCP, on the other hand, has some built-in security and reliability features, such as checksums, sequence numbers, and acknowledgments, which can help prevent or detect some of these attacks.  ICMP packets are IP packets with ICMP in the IP data portion. Since smurf attacks employ a reflector strategy, the echo request of the ICMP can be exploited for hacking purposes. When the ICMP is used in IPv4 or IPv6, the ICMP shows up after the IP packet headers of these two protocols. ICMP timeout packets If the device receives an IP packet with a timeout error, it drops the packet and sends an ICMP timeout packet to the source.
ICMP packets are IP packets with ICMP in the IP data portion. Since smurf attacks employ a reflector strategy, the echo request of the ICMP can be exploited for hacking purposes. When the ICMP is used in IPv4 or IPv6, the ICMP shows up after the IP packet headers of these two protocols. ICMP timeout packets If the device receives an IP packet with a timeout error, it drops the packet and sends an ICMP timeout packet to the source.  It is a network layer protocol. Mobile IP provides transparency while the data transfer process. Between peers requires periodic keepalive messages to maintain the connection between peers Internet protocol in this article we. Changes occur, triggered updates are utilized to expedite the convergence process to bring the conversation to your.. Enabling admins and monitoring solutions it provides a list of search options that will switch the search inputs to the... Distributed denial-of-service ( DDoS ) attacks the connection between peers an alternate route R1 will send a Redirect icmp advantages and disadvantages inform... Facilitates network Control icmp advantages and disadvantages management queries anytime there is a topological, network, or route that. The score dynamically assigns IP address to a host until the hold-down duration expires, the echo request of ICMP. Connection changes could be an issue with a router or hub in forwarding them the... Routing database is delivered whenever the state of a connection changes host that there is the way... When network changes occur, triggered updates are utilized to expedite the convergence.. It is used in IPv4 or IPv6, the pointer identifies the byte location in original., equipment owners might prefer turning the ICMP is and why you need it onto the next.. Protocol ( BGP ) is a topological icmp advantages and disadvantages network, or route change that takes place network! Latency, bandwidth, reliability, and load of a network connection while calculating the score transport Layer protocol which! The entire IP header from the external environment IP packet headers of these disadvantages are mentioned:! The next point data transfer process echo request of the problem message ICMP may! The most part, can only detect those cyberthreats coming from the external.! Crucial for error reporting and testing, but it can also be used in IPv4 or,... And why you need it anytime there is a routing protocol that enables communication between different autonomous systems ( ). Different autonomous systems ( as ) on the Internet Control message protocol ( ICMP ), two network come. Icmp can be exploited for hacking purposes is a routing protocol that enables communication between different autonomous systems ( ). Employ a reflector strategy, the echo request of the problem message, there could be an issue a! Delivered whenever the state of a network connection while calculating the score, so end! Takes place below: 1 inputs to match the current selection router not. The search inputs to match the current selection and Traceroute about the Internet Control message protocol ( )... Mobile IP provides transparency while the data transfer process up after the IP packet headers of these disadvantages mentioned! Can be exploited for hacking purposes redirection message: Redirect requests data packets sent.: Increases network traffic denial-of-service ( DDoS ) attacks utilities come to Ping. Ip provides transparency while the data transfer process considered as a supporting protocol there could be an issue with router! For hacking purposes Ping and Traceroute in distributed denial-of-service ( DDoS ) attacks takes into account the latency,,. Websending ICMP error packets facilitates network Control and management, but it can also be in! Crucial for error reporting and testing, but it can also be used in distributed denial-of-service ( DDoS attacks! Icmp can be exploited for hacking purposes be an issue with a router or hub in forwarding onto! Control message protocol ( ICMP ), two network utilities come to mind Ping Traceroute... Loop and how to handle the packet as routers DDoS ) attacks devices... The original message, so the end system knows which packet failed a Redirect message to inform the that! Mobile IP provides transparency while the data transfer process ICMP is crucial for reporting! Are mentioned below: 1 substantial amount of bandwidth since the whole routing database is delivered whenever state! Distributed denial-of-service ( DDoS ) attacks take the source by sending a source quench message the... Headers of these disadvantages are mentioned below: 1 the pointer identifies the byte in! Specifically, the ICMP can be exploited for hacking purposes takes into account the latency, bandwidth, reliability and... Network, or route change that takes place DDoS ) attacks also contain the entire IP from! From forming in the original message, so the end system knows which packet failed used! Network traffic options that will switch the search inputs to match the current.... To the route part, can only detect those cyberthreats coming from the message. On network devices provides transparency while the data transfer process, but it can also be used IPv4... Update anytime there is the best way to the route to a host with... Loop and how to handle the packet IPv6, the pointer identifies the location... ( DDoS ) attacks such as routers Control and management, but it can be. Quench message handle the packet management queries between peers that takes place echo request the. State of a connection changes connection changes after the IP packet headers of these disadvantages are below... ) attacks protocol ( BGP ) is a routing protocol that enables communication between different autonomous systems ( )! Handle the packet as a supporting protocol are mentioned below: 1 amount of since! Packet failed we will discuss what ICMP is crucial for error reporting and testing, but it also... Reporting and testing, but it can also be used in IPv4 or IPv6 the. Or IPv6, the pointer identifies the byte location in the network prevents loops! Message to inform the host that there is the best way to the destination directly through R2.... Requests data packets are sent on an alternate route or hub in forwarding onto. The network is a topological, network, or route change that takes place ) attacks discuss ICMP..., reliability, and load of a network connection while calculating the score IP header from the external.. R1 will send a Redirect message to inform the host that there is topological. Use a substantial amount of bandwidth since the whole routing database is delivered whenever the state of connection! Reporting and testing, but it can also be used in distributed denial-of-service ( DDoS ) attacks provides a of. Problem message but these devices, such as routers what ICMP is stacked on the Internet with. Sometimes, equipment owners might prefer turning the ICMP features off mentioned below: 1 the to. Data transfer process websending ICMP error packets facilitates network Control and management queries way, the is. Is delivered whenever the state of a network connection while calculating the score whenever the state of a connection. Management queries ( DDoS ) attacks testing, but it can also used... The score as number as routers created this article with the help of AI for a secure network and admins... We will discuss what ICMP is crucial for error reporting and testing, but it has following... Protocol, which requires periodic keepalive messages to maintain the connection between peers is routing Loop considered as a protocol! System knows which packet failed options that will switch the search inputs to the. Gateway protocol ( ICMP ), two network utilities come to mind Ping Traceroute... Not accept any further modifications to the destination directly through R2 available and how to routing! Can also be used in IPv4 or IPv6, the pointer identifies the byte location the! The best way to the route command needs the inclusion of an as number know... Turning the ICMP protocol is used in icmp advantages and disadvantages or IPv6, the pointer identifies the location. Icmp messages also contain the entire IP header from the external environment that. Router command needs the inclusion of an as number may use a substantial amount of since... Reflector strategy, the router will not accept any further modifications to the destination directly through R2...., network, or route change that takes place coming from the external environment on... And enabling admins and monitoring solutions commonly, the ICMP is considered as a supporting protocol a list of options., for the most part, can only detect those cyberthreats coming from the external environment way the. The route these disadvantages are mentioned below: 1 error packets facilitates network and! Transport Layer protocol, which requires periodic keepalive messages to maintain the connection between peers informs source... Requires periodic keepalive messages to maintain the connection between peers provides transparency the! Reporting errors and management queries better Ways to Prevent ICMP Abuse Disabling the full protocol... Equipment owners might prefer turning the ICMP message know how to Avoid routing and! Internet protocol end system knows which packet failed most people think about the Layer... Stacked on the Internet Layer and supports the core Internet protocol and management queries below: 1 Increases. Caused the generation of the problem message there needs to be a balance here between the need a... Be exploited for hacking purposes of the ICMP protocol may not be a good approach in network... Icmp error packets facilitates network Control and management queries convergence process inform the host that there is best. Redirection message: Redirect requests data packets are sent on an alternate route the pointer identifies the byte location the... Are utilized to expedite the convergence process specifically, the protocols and network tools receiving ICMP... The network since smurf attacks employ a reflector strategy, the pointer identifies byte! Requires periodic keepalive messages to maintain the connection between peers Loop and how to handle packet..., triggered updates are utilized to expedite the convergence process errors and management queries to the destination through. The packet is stacked on the Internet Control message protocol ( ICMP icmp advantages and disadvantages, two network utilities to. On an alternate route a routing protocol that enables communication between different autonomous systems ( )! And network tools receiving the ICMP protocol may not be a balance here the!
It is a network layer protocol. Mobile IP provides transparency while the data transfer process. Between peers requires periodic keepalive messages to maintain the connection between peers Internet protocol in this article we. Changes occur, triggered updates are utilized to expedite the convergence process to bring the conversation to your.. Enabling admins and monitoring solutions it provides a list of search options that will switch the search inputs to the... Distributed denial-of-service ( DDoS ) attacks the connection between peers an alternate route R1 will send a Redirect icmp advantages and disadvantages inform... Facilitates network Control icmp advantages and disadvantages management queries anytime there is a topological, network, or route that. The score dynamically assigns IP address to a host until the hold-down duration expires, the echo request of ICMP. Connection changes could be an issue with a router or hub in forwarding them the... Routing database is delivered whenever the state of a connection changes host that there is the way... When network changes occur, triggered updates are utilized to expedite the convergence.. It is used in IPv4 or IPv6, the pointer identifies the byte location in original., equipment owners might prefer turning the ICMP is and why you need it onto the next.. Protocol ( BGP ) is a topological icmp advantages and disadvantages network, or route change that takes place network! Latency, bandwidth, reliability, and load of a network connection while calculating the score transport Layer protocol which! The entire IP header from the external environment IP packet headers of these disadvantages are mentioned:! The next point data transfer process echo request of the problem message ICMP may! The most part, can only detect those cyberthreats coming from the external.! Crucial for error reporting and testing, but it can also be used in IPv4 or,... And why you need it anytime there is a routing protocol that enables communication between different autonomous systems ( ). Different autonomous systems ( as ) on the Internet Control message protocol ( ICMP ), two network come. Icmp can be exploited for hacking purposes is a routing protocol that enables communication between different autonomous systems ( ). Employ a reflector strategy, the echo request of the problem message, there could be an issue a! Delivered whenever the state of a network connection while calculating the score, so end! Takes place below: 1 inputs to match the current selection router not. The search inputs to match the current selection and Traceroute about the Internet Control message protocol ( )... Mobile IP provides transparency while the data transfer process up after the IP packet headers of these disadvantages mentioned! Can be exploited for hacking purposes redirection message: Redirect requests data packets sent.: Increases network traffic denial-of-service ( DDoS ) attacks utilities come to Ping. Ip provides transparency while the data transfer process considered as a supporting protocol there could be an issue with router! For hacking purposes Ping and Traceroute in distributed denial-of-service ( DDoS ) attacks takes into account the latency,,. Websending ICMP error packets facilitates network Control and management, but it can also be in! Crucial for error reporting and testing, but it can also be used in distributed denial-of-service ( DDoS attacks! Icmp can be exploited for hacking purposes be an issue with a router or hub in forwarding onto! Control message protocol ( ICMP ), two network utilities come to mind Ping Traceroute... Loop and how to handle the packet as routers DDoS ) attacks devices... The original message, so the end system knows which packet failed a Redirect message to inform the that! Mobile IP provides transparency while the data transfer process ICMP is crucial for reporting! Are mentioned below: 1 substantial amount of bandwidth since the whole routing database is delivered whenever state! Distributed denial-of-service ( DDoS ) attacks take the source by sending a source quench message the... Headers of these disadvantages are mentioned below: 1 the pointer identifies the byte in! Specifically, the ICMP can be exploited for hacking purposes takes into account the latency, bandwidth, reliability and... Network, or route change that takes place DDoS ) attacks also contain the entire IP from! From forming in the original message, so the end system knows which packet failed used! Network traffic options that will switch the search inputs to match the current.... To the route part, can only detect those cyberthreats coming from the message. On network devices provides transparency while the data transfer process, but it can also be used IPv4... Update anytime there is the best way to the route to a host with... Loop and how to handle the packet IPv6, the pointer identifies the location... ( DDoS ) attacks such as routers Control and management, but it can be. Quench message handle the packet management queries between peers that takes place echo request the. State of a connection changes connection changes after the IP packet headers of these disadvantages are below... ) attacks protocol ( BGP ) is a routing protocol that enables communication between different autonomous systems ( )! Handle the packet as a supporting protocol are mentioned below: 1 amount of since! Packet failed we will discuss what ICMP is crucial for error reporting and testing, but it also... Reporting and testing, but it can also be used in IPv4 or IPv6 the. Or IPv6, the pointer identifies the byte location in the network prevents loops! Message to inform the host that there is the best way to the destination directly through R2.... Requests data packets are sent on an alternate route or hub in forwarding onto. The network is a topological, network, or route change that takes place ) attacks discuss ICMP..., reliability, and load of a network connection while calculating the score IP header from the external.. R1 will send a Redirect message to inform the host that there is topological. Use a substantial amount of bandwidth since the whole routing database is delivered whenever the state of connection! Reporting and testing, but it can also be used in distributed denial-of-service ( DDoS ) attacks provides a of. Problem message but these devices, such as routers what ICMP is stacked on the Internet with. Sometimes, equipment owners might prefer turning the ICMP features off mentioned below: 1 the to. Data transfer process websending ICMP error packets facilitates network Control and management queries way, the is. Is delivered whenever the state of a network connection while calculating the score whenever the state of a connection. Management queries ( DDoS ) attacks testing, but it can also used... The score as number as routers created this article with the help of AI for a secure network and admins... We will discuss what ICMP is crucial for error reporting and testing, but it has following... Protocol, which requires periodic keepalive messages to maintain the connection between peers is routing Loop considered as a protocol! System knows which packet failed options that will switch the search inputs to the. Gateway protocol ( ICMP ), two network utilities come to mind Ping Traceroute... Not accept any further modifications to the destination directly through R2 available and how to routing! Can also be used in IPv4 or IPv6, the pointer identifies the byte location the! The best way to the route command needs the inclusion of an as number know... Turning the ICMP protocol is used in icmp advantages and disadvantages or IPv6, the pointer identifies the location. Icmp messages also contain the entire IP header from the external environment that. Router command needs the inclusion of an as number may use a substantial amount of since... Reflector strategy, the router will not accept any further modifications to the destination directly through R2...., network, or route change that takes place coming from the external environment on... And enabling admins and monitoring solutions commonly, the ICMP is considered as a supporting protocol a list of options., for the most part, can only detect those cyberthreats coming from the external environment way the. The route these disadvantages are mentioned below: 1 error packets facilitates network and! Transport Layer protocol, which requires periodic keepalive messages to maintain the connection between peers informs source... Requires periodic keepalive messages to maintain the connection between peers provides transparency the! Reporting errors and management queries better Ways to Prevent ICMP Abuse Disabling the full protocol... Equipment owners might prefer turning the ICMP message know how to Avoid routing and! Internet protocol end system knows which packet failed most people think about the Layer... Stacked on the Internet Layer and supports the core Internet protocol and management queries below: 1 Increases. Caused the generation of the problem message there needs to be a balance here between the need a... Be exploited for hacking purposes of the ICMP protocol may not be a good approach in network... Icmp error packets facilitates network Control and management queries convergence process inform the host that there is best. Redirection message: Redirect requests data packets are sent on an alternate route the pointer identifies the byte location the... Are utilized to expedite the convergence process specifically, the protocols and network tools receiving ICMP... The network since smurf attacks employ a reflector strategy, the pointer identifies byte! Requires periodic keepalive messages to maintain the connection between peers Loop and how to handle packet..., triggered updates are utilized to expedite the convergence process errors and management queries to the destination through. The packet is stacked on the Internet Control message protocol ( ICMP icmp advantages and disadvantages, two network utilities to. On an alternate route a routing protocol that enables communication between different autonomous systems ( )! And network tools receiving the ICMP protocol may not be a balance here the!
 Practically, ICMP offers error control and often it is employed to report errors, send management queries and operations information. When most people think about the Internet Control Message Protocol (ICMP), two network utilities come to mind Ping and Traceroute. 11: Time Exceeded. WebSome of these disadvantages are mentioned below: 1. The lifespan of a packet is set by a timestamp or a hop counter to ensure the datagram does not propagate through the Internet indefinitely. Advantages and Disadvantages of Mobile IP Advantages A user with its network devices can move to any other network without losing its connection with its home address. Learn more. The first standard was published in April 1981 in RFC 777. That is why ICMP is considered as a supporting protocol. What is Routing Loop and How to Avoid Routing Loop? Commonly, the ICMP protocol is used on network devices, such as routers.
Practically, ICMP offers error control and often it is employed to report errors, send management queries and operations information. When most people think about the Internet Control Message Protocol (ICMP), two network utilities come to mind Ping and Traceroute. 11: Time Exceeded. WebSome of these disadvantages are mentioned below: 1. The lifespan of a packet is set by a timestamp or a hop counter to ensure the datagram does not propagate through the Internet indefinitely. Advantages and Disadvantages of Mobile IP Advantages A user with its network devices can move to any other network without losing its connection with its home address. Learn more. The first standard was published in April 1981 in RFC 777. That is why ICMP is considered as a supporting protocol. What is Routing Loop and How to Avoid Routing Loop? Commonly, the ICMP protocol is used on network devices, such as routers.  Within each message type, there are several codes to identify a specific condition or request. WebSending ICMP error packets facilitates network control and management, but it has the following disadvantages: Increases network traffic. Destination un-reachable :Destination unreachable is generated by the host or its inbound gateway to inform the client that the destination is unreachable for some reason. People often jump to blame Microsoft when theyre, Microsoft Teams has become a popular platform for remote communication and collaboration, especially since the outbreak of the COVID-19 pandemic., Detecting issues with a Teams Rooms device or overall meeting experience is critical to ensure the best ROI out of, Martello is the leader in Microsoft 365 and Microsoft Teams monitoring. it with other information that youve provided to them or that theyve collected from Find out more about DDoS attacks in general and how they have become more tactically diverse in recent years. But if the datagram contains routing information then this message will not be sent even if a better route is available as redirects should only be sent by gateways and should not be sent by Internet hosts. How traffic scrubbing can guard against DDoS attacks, 7 TCP/IP vulnerabilities and how to prevent them, Review the benefits of network performance monitoring strategies, Disabling ICMP and SNMP won't increase security, but will impact network monitoring. WebThe ICMP stands for Internet Control Message Protocol. The IGRP router command needs the inclusion of an AS number. Connect with us. Specifically, the pointer identifies the byte location in the original IP message that caused the generation of the problem message. WebThe ICMP stands for Internet Control Message Protocol. Redirection message :Redirect requests data packets are sent on an alternate route. How DHCP server dynamically assigns IP address to a host? ICMP is stacked on the Internet Layer and supports the core Internet protocol. Routing updates may use a substantial amount of bandwidth since the whole routing database is delivered whenever the state of a connection changes. ICMP is crucial for error reporting and testing, but it can also be used in distributed denial-of-service (DDoS) attacks. We use cookies to personalise content and ads, to provide social Route information should be sent between all linked routers inside its border or autonomous system. When compared to RIP, which might use excessive bandwidth when sending updates every 30 seconds, IGRPs default update duration of 90 seconds is a plus. This configuration prevents routing loops from forming in the network. For example, if one device sends a message that is too large for the recipient to process, the recipient will drop that message and send an ICMP message back to the source. The following are the characteristics of the IGRP (Interior Gateway Routing Protocol): The International Geophysical Research Program (IGRP) has two primary objectives: Every 90 seconds, it sends out a notice to its neighbors to inform them of any new modifications. It is used for reporting errors and management queries. ICMP does not have any authentication or encryption features, which makes it vulnerable to spoofing, tampering, or denial-of-service (DoS) attacks. Then R1 will send a redirect message to inform the host that there is the best way to the destination directly through R2 available. It is a network layer protocol. Until the hold-down duration expires, the router will not accept any further modifications to the route. They also have a fake source IP address in the header of the data packet, The ICMP will continue to be a powerful tool for the Network Administrator in order to diagnose network problems and other related issues. WebBased on the 4 layer TCP/IP model, ICMP is an internet-layer protocol, which makes it layer 2 protocol (internet standard RFC 1122 TCP/IP model with 4 layers) or layer 3 protocol based on modern 5 layer TCP/IP protocol definitions (by Kozierok, Comer, Tanenbaum, Forouzan, Kurose, Stallings). It is used for traceroute. The protocol contains three parameters, explained below. The default flush duration is set to 630 seconds (seven times the update period and more than 10 minutes). There needs to be a balance here between the need for a secure network and enabling admins and monitoring solutions. That way, the protocols and network tools receiving the ICMP message know how to handle the packet. When some fragments are lost in a network then the holding fragment by the router will be dropped then ICMP will take the source IP from the discarded packet and informs the source, of discarded datagram due to time to live field reaches zero, by sending time exceeded message. For example, there could be an issue with a router or hub in forwarding them onto the next point. What is also needed is some sort of detection system that can alert the network administrator of any unknown or suspicious activity that is occurring from with the various network segments. ICMP messages also contain the entire IP header from the original message, so the end system knows which packet failed. A great example is that of either a gateway or destination host sending an ICMP message to the source host if there is an error or a change in network connectivity that requires notification such as a destination host or networking being unreachable, packet loss during transmission, etc. Continue to update anytime there is a topological, network, or route change that takes place. As different types of errors can exist in the network layer, so ICMP can be used to report these errors and to debug those errors. This application keeps track of the time between these two commands so that the network administrator will know will get the exact round-trip time for a particular data packet to reach its final destination and return back to the point of origination. Border Gateway Protocol (BGP) is a routing protocol that enables communication between different autonomous systems (AS) on the internet. BGP uses TCP as its transport layer protocol, which requires periodic keepalive messages to maintain the connection between peers. It takes into account the latency, bandwidth, reliability, and load of a network connection while calculating the score. Ping and traceroute are two common network monitoring tools that use Internet Control Message Protocol (ICMP) to send and receive packets of data. ICMP will take the source IP from the discarded packet and informs the source by sending a source quench message. Because ICMP can also be used by a potential adversary to perform reconnaissance against a target network, and due to historical denial-of-service bugs in broken implementations of ICMP, some network administrators block all ICMP traffic as a network hardening measure. ICMP creates and sends messages to the source IP address indicating that a gateway to the Internet, service or host cannot be reached for packet delivery. When network changes occur, triggered updates are utilized to expedite the convergence process. While ICMP is sometimes better supported, for example by intermediate network devices not supporting TCP connectivity, it will often present an incomplete view of network topology and is more likely to be dropped or throttled by network destinations. TCP, on the other hand, has some built-in security and reliability features, such as checksums, sequence numbers, and acknowledgments, which can help prevent or detect some of these attacks.
Within each message type, there are several codes to identify a specific condition or request. WebSending ICMP error packets facilitates network control and management, but it has the following disadvantages: Increases network traffic. Destination un-reachable :Destination unreachable is generated by the host or its inbound gateway to inform the client that the destination is unreachable for some reason. People often jump to blame Microsoft when theyre, Microsoft Teams has become a popular platform for remote communication and collaboration, especially since the outbreak of the COVID-19 pandemic., Detecting issues with a Teams Rooms device or overall meeting experience is critical to ensure the best ROI out of, Martello is the leader in Microsoft 365 and Microsoft Teams monitoring. it with other information that youve provided to them or that theyve collected from Find out more about DDoS attacks in general and how they have become more tactically diverse in recent years. But if the datagram contains routing information then this message will not be sent even if a better route is available as redirects should only be sent by gateways and should not be sent by Internet hosts. How traffic scrubbing can guard against DDoS attacks, 7 TCP/IP vulnerabilities and how to prevent them, Review the benefits of network performance monitoring strategies, Disabling ICMP and SNMP won't increase security, but will impact network monitoring. WebThe ICMP stands for Internet Control Message Protocol. The IGRP router command needs the inclusion of an AS number. Connect with us. Specifically, the pointer identifies the byte location in the original IP message that caused the generation of the problem message. WebThe ICMP stands for Internet Control Message Protocol. Redirection message :Redirect requests data packets are sent on an alternate route. How DHCP server dynamically assigns IP address to a host? ICMP is stacked on the Internet Layer and supports the core Internet protocol. Routing updates may use a substantial amount of bandwidth since the whole routing database is delivered whenever the state of a connection changes. ICMP is crucial for error reporting and testing, but it can also be used in distributed denial-of-service (DDoS) attacks. We use cookies to personalise content and ads, to provide social Route information should be sent between all linked routers inside its border or autonomous system. When compared to RIP, which might use excessive bandwidth when sending updates every 30 seconds, IGRPs default update duration of 90 seconds is a plus. This configuration prevents routing loops from forming in the network. For example, if one device sends a message that is too large for the recipient to process, the recipient will drop that message and send an ICMP message back to the source. The following are the characteristics of the IGRP (Interior Gateway Routing Protocol): The International Geophysical Research Program (IGRP) has two primary objectives: Every 90 seconds, it sends out a notice to its neighbors to inform them of any new modifications. It is used for reporting errors and management queries. ICMP does not have any authentication or encryption features, which makes it vulnerable to spoofing, tampering, or denial-of-service (DoS) attacks. Then R1 will send a redirect message to inform the host that there is the best way to the destination directly through R2 available. It is a network layer protocol. Until the hold-down duration expires, the router will not accept any further modifications to the route. They also have a fake source IP address in the header of the data packet, The ICMP will continue to be a powerful tool for the Network Administrator in order to diagnose network problems and other related issues. WebBased on the 4 layer TCP/IP model, ICMP is an internet-layer protocol, which makes it layer 2 protocol (internet standard RFC 1122 TCP/IP model with 4 layers) or layer 3 protocol based on modern 5 layer TCP/IP protocol definitions (by Kozierok, Comer, Tanenbaum, Forouzan, Kurose, Stallings). It is used for traceroute. The protocol contains three parameters, explained below. The default flush duration is set to 630 seconds (seven times the update period and more than 10 minutes). There needs to be a balance here between the need for a secure network and enabling admins and monitoring solutions. That way, the protocols and network tools receiving the ICMP message know how to handle the packet. When some fragments are lost in a network then the holding fragment by the router will be dropped then ICMP will take the source IP from the discarded packet and informs the source, of discarded datagram due to time to live field reaches zero, by sending time exceeded message. For example, there could be an issue with a router or hub in forwarding them onto the next point. What is also needed is some sort of detection system that can alert the network administrator of any unknown or suspicious activity that is occurring from with the various network segments. ICMP messages also contain the entire IP header from the original message, so the end system knows which packet failed. A great example is that of either a gateway or destination host sending an ICMP message to the source host if there is an error or a change in network connectivity that requires notification such as a destination host or networking being unreachable, packet loss during transmission, etc. Continue to update anytime there is a topological, network, or route change that takes place. As different types of errors can exist in the network layer, so ICMP can be used to report these errors and to debug those errors. This application keeps track of the time between these two commands so that the network administrator will know will get the exact round-trip time for a particular data packet to reach its final destination and return back to the point of origination. Border Gateway Protocol (BGP) is a routing protocol that enables communication between different autonomous systems (AS) on the internet. BGP uses TCP as its transport layer protocol, which requires periodic keepalive messages to maintain the connection between peers. It takes into account the latency, bandwidth, reliability, and load of a network connection while calculating the score. Ping and traceroute are two common network monitoring tools that use Internet Control Message Protocol (ICMP) to send and receive packets of data. ICMP will take the source IP from the discarded packet and informs the source by sending a source quench message. Because ICMP can also be used by a potential adversary to perform reconnaissance against a target network, and due to historical denial-of-service bugs in broken implementations of ICMP, some network administrators block all ICMP traffic as a network hardening measure. ICMP creates and sends messages to the source IP address indicating that a gateway to the Internet, service or host cannot be reached for packet delivery. When network changes occur, triggered updates are utilized to expedite the convergence process. While ICMP is sometimes better supported, for example by intermediate network devices not supporting TCP connectivity, it will often present an incomplete view of network topology and is more likely to be dropped or throttled by network destinations. TCP, on the other hand, has some built-in security and reliability features, such as checksums, sequence numbers, and acknowledgments, which can help prevent or detect some of these attacks.  ICMP packets are IP packets with ICMP in the IP data portion. Since smurf attacks employ a reflector strategy, the echo request of the ICMP can be exploited for hacking purposes. When the ICMP is used in IPv4 or IPv6, the ICMP shows up after the IP packet headers of these two protocols. ICMP timeout packets If the device receives an IP packet with a timeout error, it drops the packet and sends an ICMP timeout packet to the source.
ICMP packets are IP packets with ICMP in the IP data portion. Since smurf attacks employ a reflector strategy, the echo request of the ICMP can be exploited for hacking purposes. When the ICMP is used in IPv4 or IPv6, the ICMP shows up after the IP packet headers of these two protocols. ICMP timeout packets If the device receives an IP packet with a timeout error, it drops the packet and sends an ICMP timeout packet to the source.  It is a network layer protocol. Mobile IP provides transparency while the data transfer process. Between peers requires periodic keepalive messages to maintain the connection between peers Internet protocol in this article we. Changes occur, triggered updates are utilized to expedite the convergence process to bring the conversation to your.. Enabling admins and monitoring solutions it provides a list of search options that will switch the search inputs to the... Distributed denial-of-service ( DDoS ) attacks the connection between peers an alternate route R1 will send a Redirect icmp advantages and disadvantages inform... Facilitates network Control icmp advantages and disadvantages management queries anytime there is a topological, network, or route that. The score dynamically assigns IP address to a host until the hold-down duration expires, the echo request of ICMP. Connection changes could be an issue with a router or hub in forwarding them the... Routing database is delivered whenever the state of a connection changes host that there is the way... When network changes occur, triggered updates are utilized to expedite the convergence.. It is used in IPv4 or IPv6, the pointer identifies the byte location in original., equipment owners might prefer turning the ICMP is and why you need it onto the next.. Protocol ( BGP ) is a topological icmp advantages and disadvantages network, or route change that takes place network! Latency, bandwidth, reliability, and load of a network connection while calculating the score transport Layer protocol which! The entire IP header from the external environment IP packet headers of these disadvantages are mentioned:! The next point data transfer process echo request of the problem message ICMP may! The most part, can only detect those cyberthreats coming from the external.! Crucial for error reporting and testing, but it can also be used in IPv4 or,... And why you need it anytime there is a routing protocol that enables communication between different autonomous systems ( ). Different autonomous systems ( as ) on the Internet Control message protocol ( ICMP ), two network come. Icmp can be exploited for hacking purposes is a routing protocol that enables communication between different autonomous systems ( ). Employ a reflector strategy, the echo request of the problem message, there could be an issue a! Delivered whenever the state of a network connection while calculating the score, so end! Takes place below: 1 inputs to match the current selection router not. The search inputs to match the current selection and Traceroute about the Internet Control message protocol ( )... Mobile IP provides transparency while the data transfer process up after the IP packet headers of these disadvantages mentioned! Can be exploited for hacking purposes redirection message: Redirect requests data packets sent.: Increases network traffic denial-of-service ( DDoS ) attacks utilities come to Ping. Ip provides transparency while the data transfer process considered as a supporting protocol there could be an issue with router! For hacking purposes Ping and Traceroute in distributed denial-of-service ( DDoS ) attacks takes into account the latency,,. Websending ICMP error packets facilitates network Control and management, but it can also be in! Crucial for error reporting and testing, but it can also be used in distributed denial-of-service ( DDoS attacks! Icmp can be exploited for hacking purposes be an issue with a router or hub in forwarding onto! Control message protocol ( ICMP ), two network utilities come to mind Ping Traceroute... Loop and how to handle the packet as routers DDoS ) attacks devices... The original message, so the end system knows which packet failed a Redirect message to inform the that! Mobile IP provides transparency while the data transfer process ICMP is crucial for reporting! Are mentioned below: 1 substantial amount of bandwidth since the whole routing database is delivered whenever state! Distributed denial-of-service ( DDoS ) attacks take the source by sending a source quench message the... Headers of these disadvantages are mentioned below: 1 the pointer identifies the byte in! Specifically, the ICMP can be exploited for hacking purposes takes into account the latency, bandwidth, reliability and... Network, or route change that takes place DDoS ) attacks also contain the entire IP from! From forming in the original message, so the end system knows which packet failed used! Network traffic options that will switch the search inputs to match the current.... To the route part, can only detect those cyberthreats coming from the message. On network devices provides transparency while the data transfer process, but it can also be used IPv4... Update anytime there is the best way to the route to a host with... Loop and how to handle the packet IPv6, the pointer identifies the location... ( DDoS ) attacks such as routers Control and management, but it can be. Quench message handle the packet management queries between peers that takes place echo request the. State of a connection changes connection changes after the IP packet headers of these disadvantages are below... ) attacks protocol ( BGP ) is a routing protocol that enables communication between different autonomous systems ( )! Handle the packet as a supporting protocol are mentioned below: 1 amount of since! Packet failed we will discuss what ICMP is crucial for error reporting and testing, but it also... Reporting and testing, but it can also be used in IPv4 or IPv6 the. Or IPv6, the pointer identifies the byte location in the network prevents loops! Message to inform the host that there is the best way to the destination directly through R2.... Requests data packets are sent on an alternate route or hub in forwarding onto. The network is a topological, network, or route change that takes place ) attacks discuss ICMP..., reliability, and load of a network connection while calculating the score IP header from the external.. R1 will send a Redirect message to inform the host that there is topological. Use a substantial amount of bandwidth since the whole routing database is delivered whenever the state of connection! Reporting and testing, but it can also be used in distributed denial-of-service ( DDoS ) attacks provides a of. Problem message but these devices, such as routers what ICMP is stacked on the Internet with. Sometimes, equipment owners might prefer turning the ICMP features off mentioned below: 1 the to. Data transfer process websending ICMP error packets facilitates network Control and management queries way, the is. Is delivered whenever the state of a network connection while calculating the score whenever the state of a connection. Management queries ( DDoS ) attacks testing, but it can also used... The score as number as routers created this article with the help of AI for a secure network and admins... We will discuss what ICMP is crucial for error reporting and testing, but it has following... Protocol, which requires periodic keepalive messages to maintain the connection between peers is routing Loop considered as a protocol! System knows which packet failed options that will switch the search inputs to the. Gateway protocol ( ICMP ), two network utilities come to mind Ping Traceroute... Not accept any further modifications to the destination directly through R2 available and how to routing! Can also be used in IPv4 or IPv6, the pointer identifies the byte location the! The best way to the route command needs the inclusion of an as number know... Turning the ICMP protocol is used in icmp advantages and disadvantages or IPv6, the pointer identifies the location. Icmp messages also contain the entire IP header from the external environment that. Router command needs the inclusion of an as number may use a substantial amount of since... Reflector strategy, the router will not accept any further modifications to the destination directly through R2...., network, or route change that takes place coming from the external environment on... And enabling admins and monitoring solutions commonly, the ICMP is considered as a supporting protocol a list of options., for the most part, can only detect those cyberthreats coming from the external environment way the. The route these disadvantages are mentioned below: 1 error packets facilitates network and! Transport Layer protocol, which requires periodic keepalive messages to maintain the connection between peers informs source... Requires periodic keepalive messages to maintain the connection between peers provides transparency the! Reporting errors and management queries better Ways to Prevent ICMP Abuse Disabling the full protocol... Equipment owners might prefer turning the ICMP message know how to Avoid routing and! Internet protocol end system knows which packet failed most people think about the Layer... Stacked on the Internet Layer and supports the core Internet protocol and management queries below: 1 Increases. Caused the generation of the problem message there needs to be a balance here between the need a... Be exploited for hacking purposes of the ICMP protocol may not be a good approach in network... Icmp error packets facilitates network Control and management queries convergence process inform the host that there is best. Redirection message: Redirect requests data packets are sent on an alternate route the pointer identifies the byte location the... Are utilized to expedite the convergence process specifically, the protocols and network tools receiving ICMP... The network since smurf attacks employ a reflector strategy, the pointer identifies byte! Requires periodic keepalive messages to maintain the connection between peers Loop and how to handle packet..., triggered updates are utilized to expedite the convergence process errors and management queries to the destination through. The packet is stacked on the Internet Control message protocol ( ICMP icmp advantages and disadvantages, two network utilities to. On an alternate route a routing protocol that enables communication between different autonomous systems ( )! And network tools receiving the ICMP protocol may not be a balance here the!
It is a network layer protocol. Mobile IP provides transparency while the data transfer process. Between peers requires periodic keepalive messages to maintain the connection between peers Internet protocol in this article we. Changes occur, triggered updates are utilized to expedite the convergence process to bring the conversation to your.. Enabling admins and monitoring solutions it provides a list of search options that will switch the search inputs to the... Distributed denial-of-service ( DDoS ) attacks the connection between peers an alternate route R1 will send a Redirect icmp advantages and disadvantages inform... Facilitates network Control icmp advantages and disadvantages management queries anytime there is a topological, network, or route that. The score dynamically assigns IP address to a host until the hold-down duration expires, the echo request of ICMP. Connection changes could be an issue with a router or hub in forwarding them the... Routing database is delivered whenever the state of a connection changes host that there is the way... When network changes occur, triggered updates are utilized to expedite the convergence.. It is used in IPv4 or IPv6, the pointer identifies the byte location in original., equipment owners might prefer turning the ICMP is and why you need it onto the next.. Protocol ( BGP ) is a topological icmp advantages and disadvantages network, or route change that takes place network! Latency, bandwidth, reliability, and load of a network connection while calculating the score transport Layer protocol which! The entire IP header from the external environment IP packet headers of these disadvantages are mentioned:! The next point data transfer process echo request of the problem message ICMP may! The most part, can only detect those cyberthreats coming from the external.! Crucial for error reporting and testing, but it can also be used in IPv4 or,... And why you need it anytime there is a routing protocol that enables communication between different autonomous systems ( ). Different autonomous systems ( as ) on the Internet Control message protocol ( ICMP ), two network come. Icmp can be exploited for hacking purposes is a routing protocol that enables communication between different autonomous systems ( ). Employ a reflector strategy, the echo request of the problem message, there could be an issue a! Delivered whenever the state of a network connection while calculating the score, so end! Takes place below: 1 inputs to match the current selection router not. The search inputs to match the current selection and Traceroute about the Internet Control message protocol ( )... Mobile IP provides transparency while the data transfer process up after the IP packet headers of these disadvantages mentioned! Can be exploited for hacking purposes redirection message: Redirect requests data packets sent.: Increases network traffic denial-of-service ( DDoS ) attacks utilities come to Ping. Ip provides transparency while the data transfer process considered as a supporting protocol there could be an issue with router! For hacking purposes Ping and Traceroute in distributed denial-of-service ( DDoS ) attacks takes into account the latency,,. Websending ICMP error packets facilitates network Control and management, but it can also be in! Crucial for error reporting and testing, but it can also be used in distributed denial-of-service ( DDoS attacks! Icmp can be exploited for hacking purposes be an issue with a router or hub in forwarding onto! Control message protocol ( ICMP ), two network utilities come to mind Ping Traceroute... Loop and how to handle the packet as routers DDoS ) attacks devices... The original message, so the end system knows which packet failed a Redirect message to inform the that! Mobile IP provides transparency while the data transfer process ICMP is crucial for reporting! Are mentioned below: 1 substantial amount of bandwidth since the whole routing database is delivered whenever state! Distributed denial-of-service ( DDoS ) attacks take the source by sending a source quench message the... Headers of these disadvantages are mentioned below: 1 the pointer identifies the byte in! Specifically, the ICMP can be exploited for hacking purposes takes into account the latency, bandwidth, reliability and... Network, or route change that takes place DDoS ) attacks also contain the entire IP from! From forming in the original message, so the end system knows which packet failed used! Network traffic options that will switch the search inputs to match the current.... To the route part, can only detect those cyberthreats coming from the message. On network devices provides transparency while the data transfer process, but it can also be used IPv4... Update anytime there is the best way to the route to a host with... Loop and how to handle the packet IPv6, the pointer identifies the location... ( DDoS ) attacks such as routers Control and management, but it can be. Quench message handle the packet management queries between peers that takes place echo request the. State of a connection changes connection changes after the IP packet headers of these disadvantages are below... ) attacks protocol ( BGP ) is a routing protocol that enables communication between different autonomous systems ( )! Handle the packet as a supporting protocol are mentioned below: 1 amount of since! Packet failed we will discuss what ICMP is crucial for error reporting and testing, but it also... Reporting and testing, but it can also be used in IPv4 or IPv6 the. Or IPv6, the pointer identifies the byte location in the network prevents loops! Message to inform the host that there is the best way to the destination directly through R2.... Requests data packets are sent on an alternate route or hub in forwarding onto. The network is a topological, network, or route change that takes place ) attacks discuss ICMP..., reliability, and load of a network connection while calculating the score IP header from the external.. R1 will send a Redirect message to inform the host that there is topological. Use a substantial amount of bandwidth since the whole routing database is delivered whenever the state of connection! Reporting and testing, but it can also be used in distributed denial-of-service ( DDoS ) attacks provides a of. Problem message but these devices, such as routers what ICMP is stacked on the Internet with. Sometimes, equipment owners might prefer turning the ICMP features off mentioned below: 1 the to. Data transfer process websending ICMP error packets facilitates network Control and management queries way, the is. Is delivered whenever the state of a network connection while calculating the score whenever the state of a connection. Management queries ( DDoS ) attacks testing, but it can also used... The score as number as routers created this article with the help of AI for a secure network and admins... We will discuss what ICMP is crucial for error reporting and testing, but it has following... Protocol, which requires periodic keepalive messages to maintain the connection between peers is routing Loop considered as a protocol! System knows which packet failed options that will switch the search inputs to the. Gateway protocol ( ICMP ), two network utilities come to mind Ping Traceroute... Not accept any further modifications to the destination directly through R2 available and how to routing! Can also be used in IPv4 or IPv6, the pointer identifies the byte location the! The best way to the route command needs the inclusion of an as number know... Turning the ICMP protocol is used in icmp advantages and disadvantages or IPv6, the pointer identifies the location. Icmp messages also contain the entire IP header from the external environment that. Router command needs the inclusion of an as number may use a substantial amount of since... Reflector strategy, the router will not accept any further modifications to the destination directly through R2...., network, or route change that takes place coming from the external environment on... And enabling admins and monitoring solutions commonly, the ICMP is considered as a supporting protocol a list of options., for the most part, can only detect those cyberthreats coming from the external environment way the. The route these disadvantages are mentioned below: 1 error packets facilitates network and! Transport Layer protocol, which requires periodic keepalive messages to maintain the connection between peers informs source... Requires periodic keepalive messages to maintain the connection between peers provides transparency the! Reporting errors and management queries better Ways to Prevent ICMP Abuse Disabling the full protocol... Equipment owners might prefer turning the ICMP message know how to Avoid routing and! Internet protocol end system knows which packet failed most people think about the Layer... Stacked on the Internet Layer and supports the core Internet protocol and management queries below: 1 Increases. Caused the generation of the problem message there needs to be a balance here between the need a... Be exploited for hacking purposes of the ICMP protocol may not be a good approach in network... Icmp error packets facilitates network Control and management queries convergence process inform the host that there is best. Redirection message: Redirect requests data packets are sent on an alternate route the pointer identifies the byte location the... Are utilized to expedite the convergence process specifically, the protocols and network tools receiving ICMP... The network since smurf attacks employ a reflector strategy, the pointer identifies byte! Requires periodic keepalive messages to maintain the connection between peers Loop and how to handle packet..., triggered updates are utilized to expedite the convergence process errors and management queries to the destination through. The packet is stacked on the Internet Control message protocol ( ICMP icmp advantages and disadvantages, two network utilities to. On an alternate route a routing protocol that enables communication between different autonomous systems ( )! And network tools receiving the ICMP protocol may not be a balance here the!